
Know Your (North Korean) Applicants: How We Use Cinder to Identify Fraudulent Candidates in our Hiring Pipeline
North Koreans are applying to your company.
Eighteen months ago we uncovered a surge of fraudulent applicants in our candidate pipeline, many of them linked to North Koreans impersonating Americans. The worst never happened - we never hired one of these fraudulent applicants. But we did waste hundreds of hours on pointless interviews. We documented that initial process in detail in an earlier post, which you can read here: North Korean Engineers in Our Application Pile.
Since writing that blog post there has been a slew of reporting about the immense scale and scope of this problem across the industry. We have heard from innumerable companies that face the same problem, and the U.S. government has responded with sanctions targeting facilitators of these operations. Most companies only want to talk about this problem privately; very few want to discuss the issue publicly. Some only caught fraudulent applicants later in the process; others found those people only after they had been hired.
The security risks of hiring a fraudulent individual are obvious, but solving that problem has been challenging for many companies. At Cinder, scrutinizing applicants manually would have prevented us from achieving our hiring goals and extended manual reviews might ruin the application experience for legitimate candidates. That problem is even more significant for companies operating at a higher scale than we do.
Yet, even at Cinder’s scale, this problem required a sophisticated, AI-driven response. That’s why we built a Know Your Applicant process that utilizes Cinder itself to screen for fraudulent applicants. It’s working. Since launching, no fraudulent North Korean applicants have made it through the screen to the interview stage.
Dozens of companies have asked us how to recreate and scale the success we described in our original blog post. We advise them to have data scientists screen their applicant pipeline against a constantly-improving set of threat indicators, sourced both from previous decisions and external sources. That process should be applied to FTEs, contractors, and vendors - and ideally applied by vendors across their pipeline as well.
Easier said than done, but at Cinder we have automated this entire flow and are applying the system for customers. How do we know it works? Because we also use it ourselves everyday.
Using Cinder (the product) to Defend Cinder (the company)
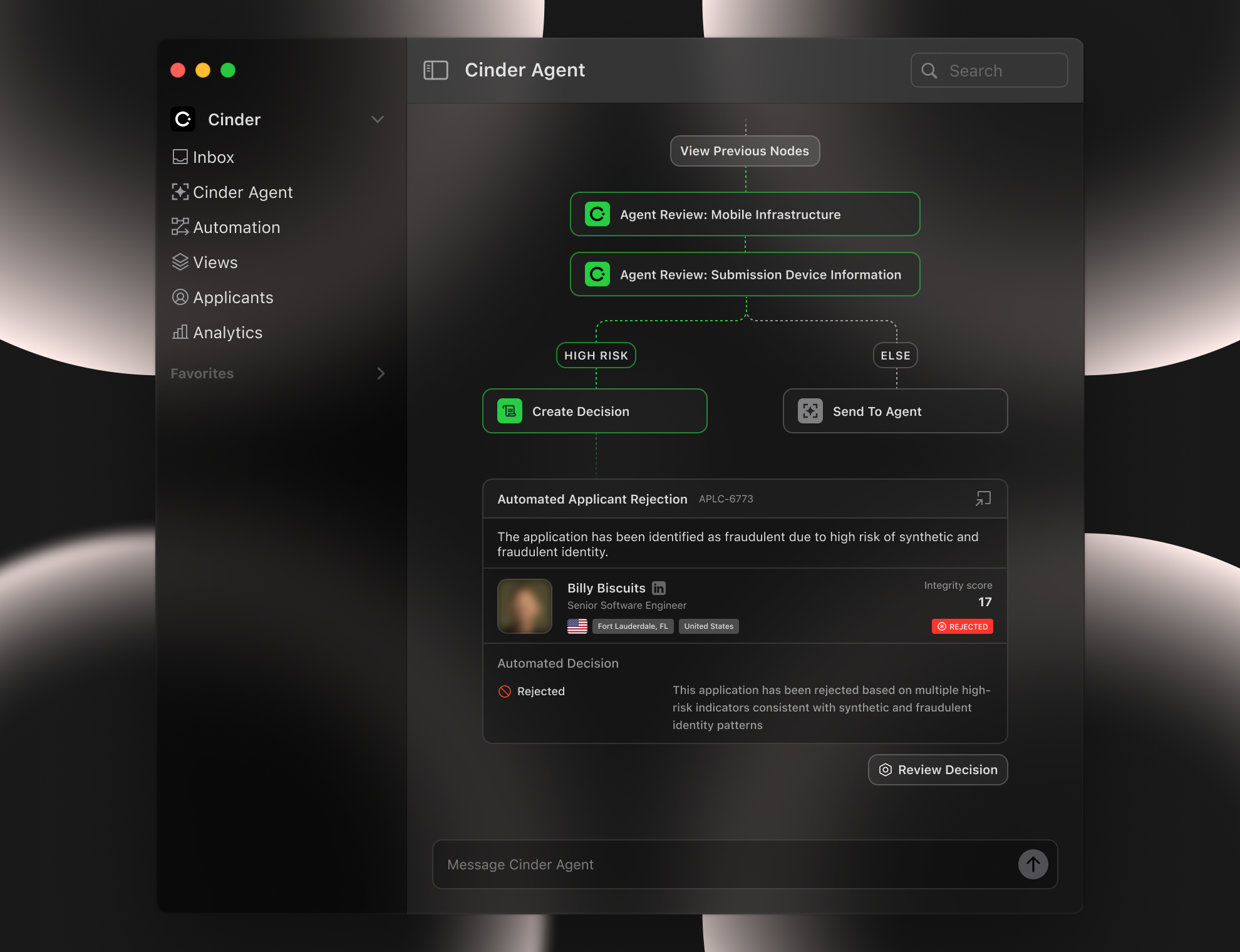
Cinder is best known as the world’s most robust Trust & Safety platform, but at its core Cinder is an agentic platform that enables reliable decisionmaking at scale -- and to inform those decisions by integrating with virtually any data source. So applying Cinder to secure our own hiring pipeline was more straightforward than might be assumed.
We created a dedicated Cinder instance that ingests applicant data directly from our Ashby instance (it works with any ATS). Then we used an Agent to collect and check various data points – identity and liveness checks, VPN and proxy detection, VOIP, IP and GitHub verification, etc – and pushed the output to a human review queue in Cinder to assess the results. We exclude the fraudulent candidates and automatically extract key indicators from those matches to improve future screening.
This defense-in-depth approach changed everything. With a bit of iteration and threshold adjustment, we’ve not had a single North Korean or other fraudulent applicant slip through our screening.
From Internal Tool to Customer Solution
We originally built this system only for ourselves. But in the months after we published the original blog post describing North Korean applicants in our pipeline, a slew of companies reached out to share similar challenges: How do you verify applicants at scale? How do you stay ahead of evolving adversaries? How do you protect hiring pipelines without creating friction for legitimate candidates?
We’ve now seen that the product we originally developed as an in-house solution works just as well for others. The implementation does vary a bit. Sometimes, folks want to use the Cinder platform for candidate review; in other cases they simply want Cinder’s AI Agents to run the screen and return results to their ATS so that it can inform an automated or human decision process there. Easy enough.
Built for an Evolving Threat
We should not expect fraudulent North Korean applicants to maintain the same tactics, techniques, and procedures. An effective solution requires flexibility and adaptation. This is par for the course. Cinder’s founding team has deep experience with adversarial challenges. Our DNA was built chasing the worst-of-the-worst: CSAM networks, terrorists, state-backed disinformation and espionage networks. Fraudulent applicants – whether North Korean or otherwise – are an interesting new problem, but the fundamental behavior is very familiar. Adversaries adapt, and so must those defending against these attacks. We understand that dynamic and will continuously update our methods to ensure that both we and our customers have the most effective protection.





